Protect your cloud infrastructure with consistent security controls across public, private, and hybrid models. Learn how to secure data and devices.
Lets chat about your Cloud Security


In today’s digital-first world, cloud security is no longer optional—it’s essential. As organizations increasingly rely on cloud computing to drive innovation and efficiency, they face a growing challenge: how to secure data, applications, and users across public, private, and hybrid cloud environments.

Each cloud model offers unique advantages. Public clouds provide scalability and cost-efficiency. Private clouds offer control and compliance. Hybrid clouds deliver flexibility by combining both. But this diversity also creates complexity. Without a unified approach to cloud security, organizations struggle to maintain visibility, enforce policies, and protect sensitive data.
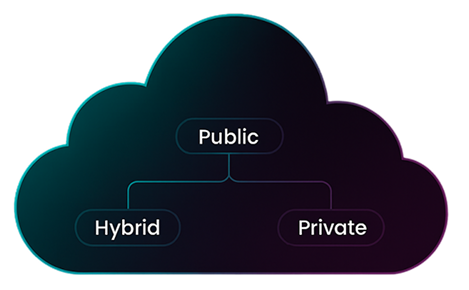


When security controls vary across environments, vulnerabilities emerge. Devices connecting to the cloud—whether laptops, mobile phones, or IoT devices—may not follow the same protocols. Data ingressing and egressing the cloud can be exposed to threats if not properly encrypted or monitored. These inconsistencies can lead to data breaches, compliance failures, and reputational damage.
Most companies don't realize they are using multiple cloud platforms. We help discover and layer in a consistent security strategy.
Use identity and access management (IAM), encryption, and real-time monitoring to secure shared resources.
Encrypt your Wi-Fi network using WPA3, the latest and most secure encryption standard. This helps prevent unauthorized access to your network.
Implement advanced threat detection, segmentation, and compliance controls for sensitive workloads.
Apply unified security policies and centralized visibility tools to manage risk across interconnected systems.
A strong cloud security posture builds trust, reduces risk, and supports business growth. Whether you're migrating to the cloud or optimizing an existing deployment, now is the time to standardize your security approach. Protect your data. Secure your users. Strengthen your future.